Yesterday I posed this quote from someone:
The constitution is the conservative equivalent of a gun-free zone.
I followed up with this deliberately very open ended question:
Now, can we use that insight and turn it into what needs to be done next?
The comments indicated everyone took a much narrower view of things than I had. One even took bizarre break from reality saying that my post meant I, “decided to go full-on Brownshirt/Blackshirt/Silvershirt” regarding the election. What? I wasn’t even talking about the election. How did they get there? Did they think they were able to read my mind through the Internet? That was really weird.
Here is what actually happened.
When I read the quote it was like first few nanoseconds of the big bang. Out of nothing there exploded a whole universe. It was like how some people describe their first LSD experience. I’ve never used LSD so I wouldn’t know for certain but that is my best analogy for how it affected me.
There were three comments (here, here, and here) which accurately touched an extremely small fraction of that universe that I saw unfold. And it was all about the past and the present. I was hoping for something more about the future as I was pretty sure I had explored enough of the past and present and satisfied myself that there wasn’t a whole lot more to be learned from those domains. I could be wrong about that so I present that part of my expanding universe for comments, corrections, and additional observations.
But what I really want is for people to think about and suggest a solution to the problem that can be implemented in the near future.
The Past
The authors of the constitution could have set up a separate branch of government which had the job of enforcing the adherence to the original intent. If not this then at least explicitly given the Federal courts some independent enforcement capability and protection from court packing. This may not have been practical or even possible but an attempt in this direction might have made some difference.
This attempts to address the issue, as McChuck, in the comments said, “The Constitution failed because it had no “OR ELSE” clause.”
At numerous critical times there were fairly clear cut issues before the courts which probably, at least a simple majority of people decided the Constitution was inadequate for the present circumstances. And rather than go the long route and get an amendment to the constitution through the process the courts allowed a short cut. This short cut was then used for things not nearly so clear cut. The short cut became a super highway with no restrictions.
I haven’t done the research but a couple very early, reasonably well known examples of such “clear cut issues” were the Lewis and Clark expedition and the Louisiana Purchase. Where does the constitution allow that in it’s enumerated powers?
There are probably hundreds if not thousands of case where little short cuts were taken over the centuries and they enabled all kinds of criminal trespass on the constitution.
What if, instead of politicians and judges instead of giving these short cuts a blind eye, they had handled it differently? What if they had said, “I think this is a good idea. I think this is within to domain of proper government power. BUT, it is also outside of the powers granted to the government”? Let’s, as rapidly as is practical, push through a narrowly scoped constitutional amendment to address this “clear cut issue”. This would have at least attempted to prevent the short cut from becoming a superhighway.
But the politicians of the time didn’t see, didn’t care, or wanted the superhighway and neither of those things happened.
The Present
The U.S. government debt is almost $28 trillion with $159 trillion in unfunded liabilities and constantly going up. Had the original intent of the U.S. constitution been adhered to that could not have happened. The superhighway of criminal trespass on the constitution is is a superhighway to disaster.
The criminal trespass on our personal liberties are just as gargantuan as the economic disaster. The First, Second, and Fourth enumerated rights in the Bill of Rights may have the most lanes of the superhighway over them but all of them, with the possible exception of the Third Amendment, have been paved over with at least a bike path clearly marked where there was once a tall fence with no gate and a NO TRESPASSING sign on it.
People who believe the constitution should be respected according to original intent started talking with each other. The Internet made it far easier to connect with others of a similar mindset. They realize, “Not only is the government infringing upon our rights, the courts aren’t coming to our aid.”
The criminals see the Internet chatter and see erosion of their voting base as more people come up to speed on the situation. The criminals shadow ban people. They freeze their accounts for a day or a week. Then they start completely banning people.
This couple was completely banned by Facebook and they have little* to no idea what it was about. A few weeks later they were both banned within minutes of each other from Instagram. All they posted on Instagram were family pictures. No explain was given. No appeal was possible.
Other people have received some clues. And it’s over the tiniest of stuff:
They are making every post of mine with #DontCaliforniaMyTexas as hate speech and deleting it. I got one day in jail for it
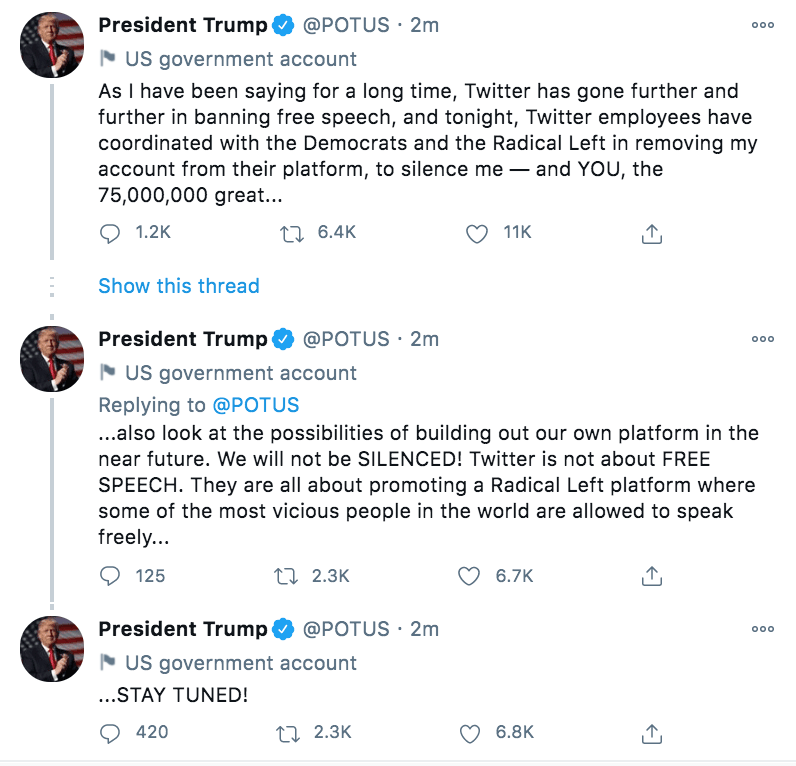
In the last week it was the President of the United States who permanently banned from Twitter. Shortly after POTUS moved to Parler, Apple, Google, and Amazon in a matter of just a few days deplatformed their apps and then the entire site. Poof! Gone! The company is possibly permanently destroyed.
Yesterday morning AR15.com was booted from GoDaddy (see also here). They are now back up on AWS Amazon. I wonder how long that will last as AWS Amazon was the host for Parler.
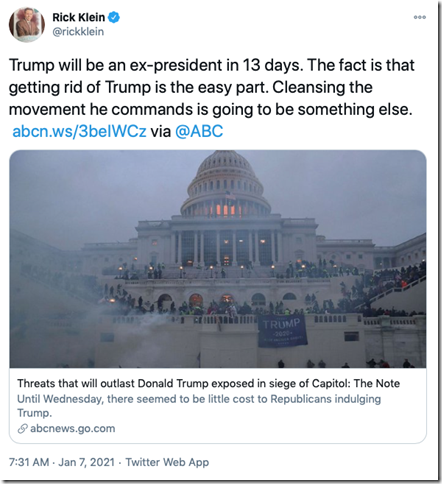
The political left is saying, “It’s time..” and “Cleansing the movement…” is next.
“Maybe they are being hyper sensitive to people of any political persuasion”, you suggest. It doesn’t look like that to me and others:
Big Tech did not remove House Speaker Nancy Pelosi’s accounts when she called for “uprisings” against the Trump administration. Facebook and Twitter did not target Alexandria Ocasio-Cortez when she claimed that allegedly marginalized groups have “no choice but to riot.” These platforms did not act against Kamala Harris when she said the riots “should not” stop.
This week, Joe Biden condemned the Capitol rioters, saying, “What we witnessed yesterday was not dissent, it was not disorder, it was not protest. It was chaos. They weren’t protesters, don’t dare call them protesters. They were a riotous mob, insurrectionists, domestic terrorists. It’s that basic, it’s that simple.”
Yet he refused to speak in those terms when Black Lives Matter and antifa militants were throwing Molotov cocktails at federal buildings, setting up “autonomous zones,” and burning down cities. Instead, he condemned Trump for holding up a Bible at a church — without mentioning the fact that that very church had been set on fire the night before.
What makes you think it will end with social media? What if the political left pulls your Internet connection for some flimsy excuse, or none at all? You think that would be going too far because Internet is essentially a requirement of life these days? Really? You think that would stop them? Do you think I am extrapolating way out into never-never land? “That can’t happen here?”
What if banks refused to do business with you. Wouldn’t that be worse than pulling your Internet connection? Guess what…The Obama administration was telling banks, “If you do business with risky customers, such as gun manufactures or dealers, you will suffer the consequences.” It was called Operation Choke Point.
What about other services such as FedEx, UPS, USPS, your water, waste disposal, and electricity? They didn’t “censor” you, you can still print a newsletter or hold a sign up on the street corner, right? And as long as it wasn’t a government entity refusing you service it’s entirely legit, right?
It used to be motels, restaurants, gasoline stations, etc. could, and did, refuse service to people based on their own criteria. There was a Federal law passed which prohibited such discrimination when it was based on the grounds of “race, color, religion, or national origin.” But it doesn’t protect you if you happen to be one of those nasty people who believe the constitution means what it says.
Do not be surprised if there aren’t soon “blacklists” that result in a surprising number of restrictions on what we normally consider public services. Don’t think so? Today Senator Chuck Schumer called for authorities to add the Capitol rioters to a national no-fly list.
The net result of this? Individual constitutionalists are, metaphorically, standing on some random street corner holding up homemade signs saying, “Repent! The End is Near!” Thousands of criminals occasionally glance at the “Gun-free zone” sign as they zoom by on the nearby superhighway at 100+ MPH and snicker.
The comparisons to the early days of what is described in Gulag Archipelago are eerie. Have a chat with someone with Venezuela, or East Germany sometime.
The Future
This is where I was/am hoping to get some discussion. How can we regain a limited government and our personal liberties?
An armed rebellion? Maybe. But I’m not seeing that as a high probability path. I could see that bringing down the government. But I don’t see that as necessarily building a consensus for the resurrections of limited government rising from the ashes. And your going to start your own cancel culture with a scoped rifle? And how does that work out? You shoot every politician with a ‘D’ beside their name? Then what? Hold another election with the same people voting (and/or cheating) as last time?
And at what point to you start shooting? Are you justified in shooting if you get booted off Facebook or Twitter? And who would you shoot if you somehow managed to convince yourself it was justified? Who do you shoot if some anonymous bureaucrat told your bank to stop doing business with you?
What’s the path to victory here? I am a details oriented guy and as I dig into the details I’m not seeing a viable path.
There is the Lyle option, as I like to think of it. A (supposed) return to Protestant values. This is, perhaps, due to the Second Coming—this isn’t entirely clear to me. I largely dismiss this, not just because I don’t believe in the existence of god(s) but because if the constitution was originally divinely inspired then why did it go so terrible wrong and how can we expect to be better the second time around?
The best I have been able to come up with is that we are probably headed for a Minsky Moment and/or a currency crisis in the somewhat near future. This could be a worldwide event and it could involve the collapse of our currency and perhaps our government. Perhaps out of the ashes of the collapse a more constrained government will have more appeal and will rise.
I see this second option as more probable of success, but still improbable, because the government size proved to be its own downfall rather than being brought down by individualist rebels. Clear and positive proof of big government failure is probably required to convince a majority of people to try small government again.
What I don’t see is a high probability of success path that can be traversed by a few people on the street corners with their handmade signs.
Please discuss.
* Barron recently told me, “I may have been tagged because I didn’t use the complete spelling of my last name.” Yet I know people who have been using completely, and pretty obviously, fake names for their Facebook accounts for years.