From Leaked Slide Shows NSA Celebrated Victory Over Google’s Security With A Smiley Face: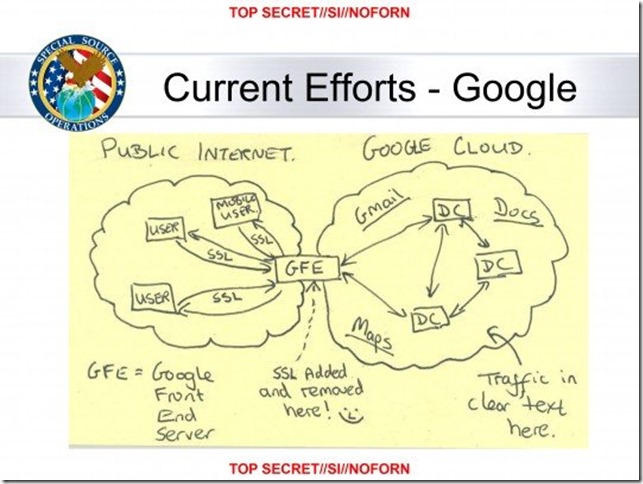
That’s good to know. What that means is that either they can’t break the encrypted messages directly or that it is more work to do so. So they do it by attacking the Google servers that do the encryption and decryption.
That means encrypting my data on my computer before it hits the Internet makes it more difficult or impossible for the NSA to read. Hence:
jfFMMWu3VNTJs0iuzM/h1J9wEDojd3+34PNTyb/u/rEnedy3y9YywxRPtP8wX5nZ13xfkduP
/7+vNFbz7150wnHv8+hyEiubOLVB2D4e2Qu62jVS6E9M7q47BGCgv59S/vhV6EKhJ3GyfqK
taan8ss0V+fBjZbpsBGbhsRXaHT+A8tXSx3DpApmVbc4MIzHr9w8WG5pzCSBI/F2CXjqTE8
EMu/5zmxm+XmawdM4IAtPotIiLDTsw8IoHVJFAMdlagQDlla2z5fGJoZlDu7fsrFu7SYTso
5gEJUZF8eju5sWsqfZp1i8KvdFPYuXbzBdKJYCg/Hq0iD3/yGr4TeuW0yZ4Xrx20Wmv3nit
rOhrWZVAOsbfYB6LgoP8j2w0UkJPtzSr3d+zWk80EDMvsuPgnA93Sn5A+omipxXTimZes6Y
nz0NyXO745pZcOH3CNlddW8AFqQ0KlJC5qNVejPRs3rEQL5y+/pXyEd8JHIo0M2Qm+Elrdn
ZwZLSmNHfCeQk7aNAfD3lHTsaCQmbTZzBVWmq1YFDxiJU5ZJGNy3pXw7LT5BUVXLV9ShlSs
RGbZObCH9W8SaMrW7hu9VBJjYvpXftv0+SpbkTcxRS2IXt1Tfuqi8VgtRyJuDf7uk3wGgmI
4Pip7A/FzAwZFCqSy3zKpkVLNg/Bvos390Y5bATdDIvefJq/4QXS/gfJZkLaDUR1+bhxhBW
tRYdi2Rto3B/+hFZ8GpFCGMQpnJBXmoPsUgNtHKkfYC9PsC6dv7iP9U1NRb5KFiRzsUAutD
9blIUkogSwFvc+zyx4YX7zdY1cMLOqmLbIpep8p2TlStjSj2w6LFQddJUQxwSHSJrd3yVlo
jWtxIJU8FvopqR/LUMBjrAG7bYddOWvbuxFF6Pk/UthK12Ih138Na7OdvuTzkQQmjhXdk9z
o/zjyNyZZAVaFsZa0h/RxQjyZUEihMtEMZDXKZNHgtU3urMkQOTR9k1MZahmhbJtEydMiGJ
6ESoyejbMzD1eqzxmZkIXMrZ3VQfPf1lUxjTPwdOoLtzTbUHvuA02vpd9Gx6L0xbqgn7obb
81TAkuYb4SWn+J7gF8Fi7FVwGFZ2V692KQ05lNDP4mWkGoAGuLZmqjvlee6TqXmIaEE0YWz
HVpvRfsdvpZNQxd

Nah, encrypting my email is too much work- I’m just gonna send it plaintext with a block of gibberish in the middle as if it were encrypted. I wonder how many cycles the NSA will waste if we all do it? Note to self: learn about steganography in order to embed anti-NSA obscenities preceded by gibberishtext to get their attention.
Aw heck; I can read that.
“Joe,
Please pick up a half gallon of milk (2%) on your way home.
Thanks,
XOXO
Barb”
Sorry. You got it mixed up with the text message she sent. That wasn’t in the blog post.
You need to tell me how you intercepted that text message some day.
😉
While the urge to tweak the NSA with blocks of gibberish appearing to be MIME code is attractive, one would probably do better to avoid attracting their attention. Bureaucracies like the NSA are never noted for their sense of humor and one would do better to fly under the radar.
For certain values of “better” you are correct.
There is just one problem with your theory: Unless you “air-gap” the machine you encrypt and decrypt on, it’s likely that they can compromise your computer and read the plaintext. And they have done just that in some cases.
If you were really, really, *REALLY* paranoid, you’d use a strong method of manual encryption (ie., paper and pencil). You can’t put a keylogger on a pencil or pen, and if you’ve never put the plaintext on a machine, it can’t be read off a machine. Plus, if you properly destroy the worksheet by burning it, they can’t get the plaintext that way. They are *FORCED* to break it cryptanalytically. And you can use methods that are highly resistant to cryptanalysis. For example, one might use memorized phrase to generate a straddling checkerboard to convert the message to numbers, then use a second phrase to generate a repeating key that you add to the numeric plaintext using modulo 10 (ie., non-carrying) addition, a third key phrase to control a columnar transposition, and a fourth for a second, interrupted transposition. Memorize four phrases, and you’ve got a key, and such a cipher would be very resistant to cryptanalysis.
Or you could use the “nuclear option”, and encrypt using one time pads. Numeric one time pads can be manually generated relatively easily and quickly using 10-sided dice, and you can use a straddling checkerboard to convert the plaintext to numbers, and just add the key using modulo 10 addition. Decryption is just the opposite, and so long as you follow the simple, ironclad rules of OTP use, the information is safe forever.
You have some valid points. But there is no safety forever. If “they” target you specifically they can gain physical access to your home and get even the one time pads.
Penetrating through any and all routers is a bit more challenging. Open source for the routers make it unlikely deliberate backdoors exist. Vulnerabilities may still exist but will be expensive to find and are subject to sudden “disappearance”. Again physical access defeats it.
The bottom line is that as long as physical access exists they can defeat any encryption.
They have teams that are very, very good at physical access.
I have other motives with the “gibberish” in my posts.
I think you’re forgetting the universal decryption algorithm: RHD
http://xkcd.com/538/
First, one time pads are resistant to “rubber hose crytpanalysis”. No one can remember the proper sequence of hundreds, or thousands, of random letters, no matter how much you drug them and beat them with a $5 wrench.
Secondly, physically securing the pads in a tamper-evident container in a hidden location is pretty easy. Even something as prosaic as gluing all the pad pages together so that they must be torn off individually goes a very long way to preserving security.
So long as you know when the pads have been accessed by unauthorized personnel, security is maintained, and perhaps even enhanced: It allows you to send deliberately false messages knowing that they will be believed. Your alleged insurrection or terrorist plot just became an embarrassing gay love affair.
The *ONLY* time this would be a problem is if they managed to read a pad page after Alice sent a message, but before Bob received it and decoded it, because good security practice is to destroy the pad as soon as you are finished with it. Even then, though, that only permits them to read that one message. It doesn’t allow them to read previous ones, and it won’t allow them to read future ones provided you can tell that the pad has been tampered with.
“good security practice is to destroy the pad as soon as you are finished with it.”
Tell that to the Navy. I eventually quit burning the codes on sked after swapping to the new day ‘cuz
“we have fighters aloft and they’re still using the old codes, so put the old one back in.”
“I can’t, I destroyed it as per established procedure. Why don’t you guys ever tell me ahead of time to keep using the old code?”
“Because it’s your responsibility to know what we want before we know it ourselves.”
“Tell me again why I re-upped? Sigh.”
They may have teams that are very, very good at physical access, but they’d be hard pressed to enter a dwelling that is usually occupied, find the pads (which are about the size of a pack of gum and can literally be hidden just about anywhere), copy them somehow without leaving any evidence of access, and then leave.
Remember, this has to be completely undetected because any noticeable sign that the pads have been tampered with in some way will result in them no longer being “trusted”.
In fact, I’ve never heard of that being done with any of the spies that have been caught. Generally, the first time the government gets its hands on the pads are during a search incident to the arrest of the agent.
Heh, I first looked at and saw “GFE” and thought “government furnished equipment.”